
The Case Vault
These organizations were breached. Your mission: review the digital evidence, reconstruct the events, and uncover who was behind it and how they got in.
Easy
This is the start of your KC7 journey. You don’t need to know much— we give you the questions and starter KQL so you can focus on the story and how evidence fits together. You’ll leave with quick wins and the core “investigator mindset.”
 - Recording mic.png)
A Rap Beef: An Intro to Security Investigations
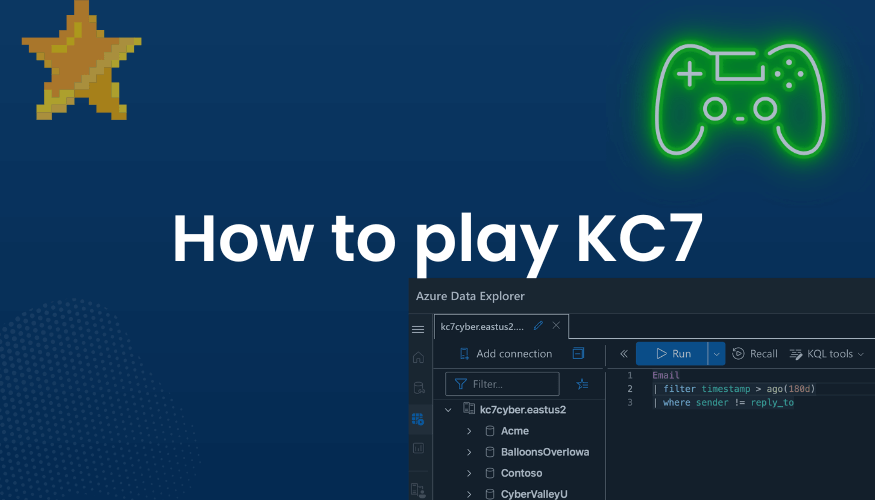
How to play KC7

CloutHaus: Social Media leads to Compromise
A Scandal in Valdoria: A Political Mystery

Valdoria Votes: A Political Mystery (Part 2)
Jojo's Hospital: A Ransomware Investigation
Solvi Systems: A tale of Supply Chains and ICS
Moderate
In this section, the training wheels start to come off. You’ll translate questions into your own KQL and spot repeating patterns. Expect growing confidence and fewer “wait…what is that?” moments.

Frognado in Valdoria: A Political Mystery
Critical Compromise In Chicago - ICS

Envolve Labs: With a twist!

Castle & Sand: A Beachy Case of Ransomware

AzureCrest - The full version
Turkey Bowl
Krusty Krab: A Intro to Pivoting and Analysis

French Socksess Story
HopsNStuff: An Easter APT hunt
Challenging
Now you choose where to look and why. You’ll connect clues across multiple logs, write multi-step queries, and explain your reasoning like a pro. Mistakes are part of the reps—your intuition gets sharper every case.
Inside Encryptodera: An Insider Threat Scenario

Galaxy Neura

System Shutdown at Azure Crest! (Short Version)
Balloons Over Iowa

Scholomance: Secrets and Lateral Movement
Dai Wok Foods: A Challenging Culinary Mystery
Hard
In these games, guidance is minimal and the intrusion is messy (just like real life). You’ll sketch a plan, pivot across data sources, validate each finding, and adjust on the fly. Expect fewer hints, more strategy, and satisfyingly hard-won answers.
Spooky Sweets: Sweet Sweet Pivots
Sunlands: A Tough Space Investigation

World Domination Nation
Ship ahoy! An Unusual Ransomware Investgation
Don't Bother
Fleeeee!!! I mean, err... You’re driving the whole investigation—scope it, hunt it, prove it, tell the story. We give you the case; you deliver conclusions backed by evidence and a clean narrative. Expect portfolio-ready work and the “I can handle new stuff” confidence that senior analysts rely on.
MCJ Walker: An Impossible Identity Crisis

A Rap Steak: A Tough Musical Affair
Arcade
This is a collection of games outside of our learning paths

DAILY7 🌎

KQL 101: An introduction to Kusto Query Languge
KQL 201: An Intermediary Course on KQL
VirusTotal Fundamentals
Titan Shield: A showcase of Microsoft Defender XDR
Empire Health
A Storm Is Brewing In the Lab
Whiskermania: An Intro to Network Concepts
A Rap Beef: An Intro to Security Investigations
 - Recording mic.png)
About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
How to play KC7

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
CloutHaus: Social Media leads to Compromise

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
A Scandal in Valdoria: A Political Mystery

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Valdoria Votes: A Political Mystery (Part 2)

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
Jojo's Hospital: A Ransomware Investigation

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Solvi Systems: A tale of Supply Chains and ICS

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Frognado in Valdoria: A Political Mystery

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Advanced Topics
Critical Compromise In Chicago - ICS

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Envolve Labs: With a twist!

About This Game
Learning Objectives
Advanced Topics
Domain-Specific Knowledge
Castle & Sand: A Beachy Case of Ransomware

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
AzureCrest - The full version

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
Turkey Bowl

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Krusty Krab: A Intro to Pivoting and Analysis

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
French Socksess Story

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
HopsNStuff: An Easter APT hunt

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Inside Encryptodera: An Insider Threat Scenario

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
Galaxy Neura

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
System Shutdown at Azure Crest! (Short Version)

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Balloons Over Iowa

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Scholomance: Secrets and Lateral Movement

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
Dai Wok Foods: A Challenging Culinary Mystery

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Spooky Sweets: Sweet Sweet Pivots

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Advanced Topics
Sunlands: A Tough Space Investigation

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Advanced Topics
World Domination Nation

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Advanced Topics
Ship ahoy! An Unusual Ransomware Investgation
About This Game
Learning Objectives
Advanced Topics
Core Analyst Competencies
MCJ Walker: An Impossible Identity Crisis

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
A Rap Steak: A Tough Musical Affair

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
DAILY7 🌎

About This Game
Learning Objectives
KQL 101: An introduction to Kusto Query Languge

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
KQL 201: An Intermediary Course on KQL

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Advanced Topics
VirusTotal Fundamentals

About This Game
Learning Objectives
Advanced Topics
Core Analyst Competencies
Domain-Specific Knowledge
Titan Shield: A showcase of Microsoft Defender XDR

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
Empire Health

About This Game
Learning Objectives
Core Analyst Competencies
Domain-Specific Knowledge
A Storm Is Brewing In the Lab

About This Game
Learning Objectives
Domain-Specific Knowledge
Core Analyst Competencies
Advanced Topics
Whiskermania: An Intro to Network Concepts


.png)